Syslog is a standard on devices for recording events and errors in a consistent format. This allows different programs to understand the messages. System administrators use syslog to track how systems are running and troubleshoot problems. Its messages are usually sent to a central server for analysis and storage.
What is Syslog and How it Works
Syslog is a standard for message logging that allows software applications and devices to send log messages to a centralized log management system. It was first introduced in the 1980s as part of the Unix operating system and has since become a widely adopted standard across various platforms, including Linux, Windows, and network devices. The primary purpose of syslog is to collect and manage log messages from different sources, such as servers, network devices, and applications, in a centralized location. This centralized log management approach makes it easier to analyze and monitor system events, security incidents, and application behavior across an entire IT infrastructure. 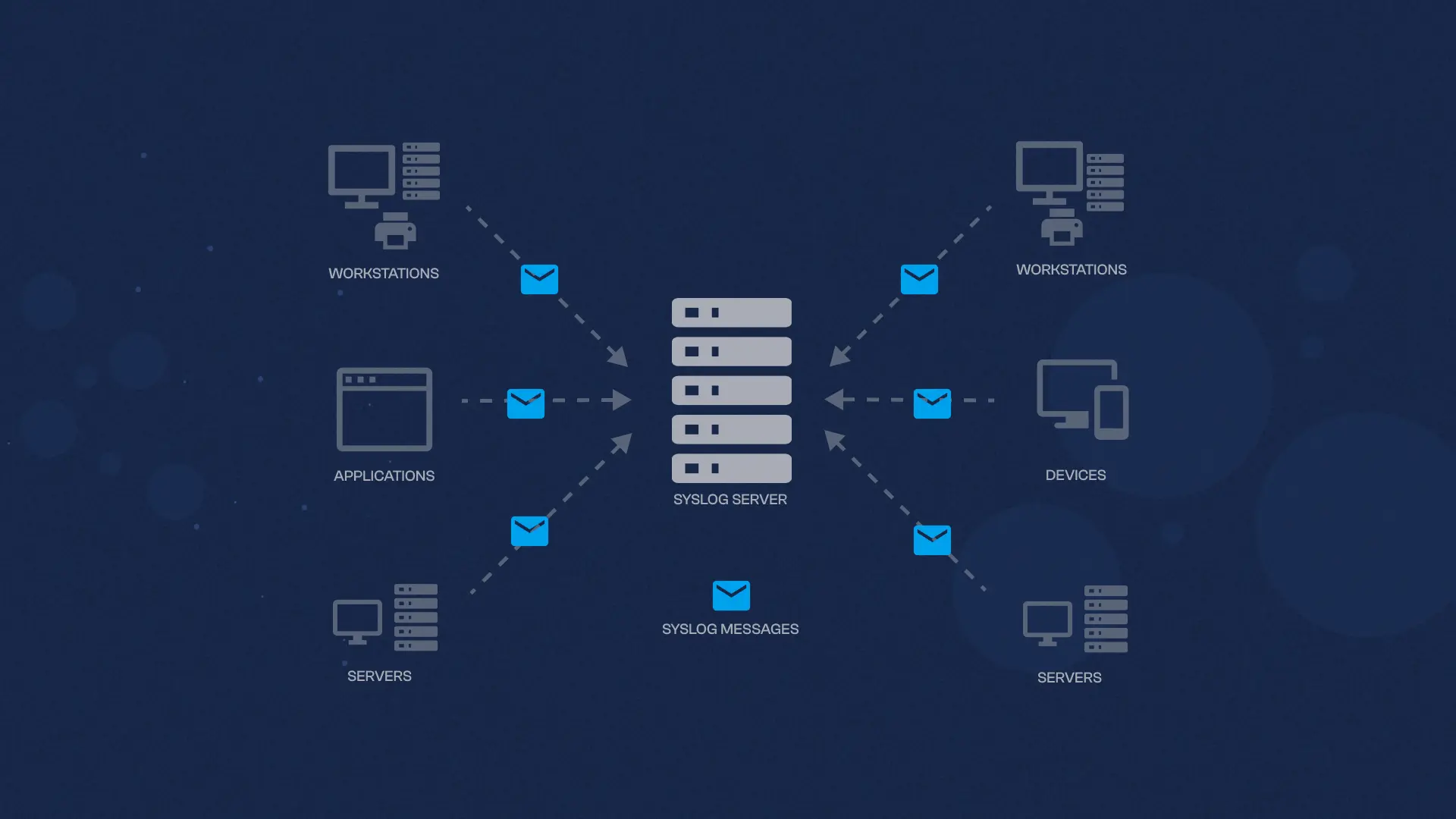
How Syslog Works
At its core, syslog operates on a client-server architecture. The syslog client (often referred to as the syslog sender or syslog agent) is responsible for generating log messages and sending them to a syslog server (also known as a syslog receiver or syslog daemon). The syslog server receives and stores these log messages, making them available for analysis, monitoring, and troubleshooting purposes.
Log Generation
Applications, systems, and devices generate log messages based on predefined events or conditions. These log messages typically include details such as the date and time, the source of the log message, and a descriptive message. The syslog format helps standardize these messages, making them easier to interpret.
Log Forwarding
The syslog client forwards the log messages to a designated syslog server using the syslog protocol. The syslog protocol supports both UDP (User Datagram Protocol) and TCP (Transmission Control Protocol) for message transport, with TCP providing reliable delivery but potentially slower performance than UDP.
Log Reception
The syslog server listens on a specific port (typically port 514 for UDP or port 601 for TCP) and receives log messages from multiple syslog clients. Configuring the syslog port correctly is crucial for ensuring that log messages are received without issues.
Log Storage
The syslog server stores the received log messages in a log file or a database, depending on the server’s configuration and requirements. Tools like rsyslog and syslog-ng offer advanced options for log storage and processing, supporting both traditional log files and more complex storage backends.
Log Analysis
System administrators, security analysts, and automated tools can access and analyze the centralized log data stored on the syslog server to gain insights, identify issues, and monitor system and application behavior. Syslog analyzers and visual syslog servers can help in visualizing and making sense of the log data.
Understanding Syslog Messages
Syslog messages follow a specific format that includes several components, making it easier to identify the source, severity, and other relevant information about the logged event. Understanding the structure of syslog messages is crucial for effective log analysis and troubleshooting.
Facility Codes
Facility codes are used to categorize the source or type of the log message. They help identify the software or component that generated the log entry. Common syslog facility codes include:
- 0 (kern): Kernel messages
- 1 (user): User-level messages
- 2 (mail): Mail system messages
- 3 (daemon): System daemon messages
- 4 (auth): Authentication and authorization messages
- 5 (syslog): Messages generated by the syslog process itself
- 6 (lpr): Line printer subsystem messages
- 7 (news): Network news subsystem messages
Severity Levels
Syslog messages are assigned a syslog severity level, indicating the logged event’s importance or urgency. The severity levels, ranging from 0 (Emergency) to 7 (Debug), are as follows:
- 0 (Emergency): System is unusable
- 1 (Alert): Action must be taken immediately
- 2 (Critical): Critical conditions
- 3 (Error): Error conditions
- 4 (Warning): Warning conditions
- 5 (Notice): Normal but significant conditions
- 6 (Informational): Informational messages
- 7 (Debug): Debug-level messages
The severity level helps administrators quickly identify and prioritize critical issues or events that require immediate attention. For instance, which syslog severity level indicates a debugging message? It’s level 7 (Debug).
Syslog Message Format
A typical syslog message follows a standardized format that includes several fields:
<Priority>Timestamp Hostname Process[PID]: Message
- <Priority>: This field combines the facility code and severity level into a single numerical value.
- Timestamp: The date and time when the log message was generated.
- Hostname: The name or IP address of the host or device that generated the log message.
- Process[PID]: The name of the process or application that generated the log message, along with its process ID (PID).
- Message: The actual text message describing the logged event or condition.
Syslog Protocol
The syslog protocol defines the standard for transmitting log messages between syslog clients (senders) and syslog servers (receivers). It specifies the format and structure of the log messages, as well as the methods for transporting them over the network. The syslog protocol supports two primary transport mechanisms:
UDP (User Datagram Protocol)
UDP is a connectionless protocol that offers faster performance but does not guarantee reliable delivery of log messages. It is commonly used for syslog due to its simplicity and efficiency, especially in high-traffic environments. Linux syslog implementations often use UDP for their speed.
TCP (Transmission Control Protocol)
TCP is a connection-oriented protocol that ensures reliable delivery of log messages by establishing a persistent connection between the client and server. While it may be slower than UDP, it provides additional reliability and supports features like message acknowledgment and retransmission. The syslog protocol operates on standardized port numbers:
- UDP syslog typically uses syslog port 514
- TCP syslog typically uses port 601 (officially assigned) or sometimes port 514 (for compatibility reasons)
It’s important to note that while the syslog protocol itself is standardized, different implementations (such as syslogd, rsyslog, and syslog-ng) may introduce additional features or variations in message formats and transport mechanisms.
Syslog Servers and Syslog Clients
Syslog Servers
A syslog server, also known as a syslog receiver or syslog daemon, is a centralized log management system that receives and stores log messages from various sources (syslog clients). Its primary functions include:
- Listening for incoming syslog messages on a designated port (typically 514 for UDP or 601 for TCP).
- Receiving and processing log messages from multiple syslog clients.
- Storing log messages in log files, databases, or other storage mechanisms for long-term retention and analysis.
- Providing tools or interfaces for log analysis, filtering, and reporting.
Syslog servers can be implemented using various software solutions, including open-source projects like rsyslog, syslog-ng, and commercial offerings from vendors like Splunk, Graylog, and others.
Syslog Clients
A syslog client, also known as a syslog sender or syslog agent, is a software component or application that generates log messages and sends them to a designated syslog server. Syslog clients can be found in various systems and devices, such as:
- Operating systems (Linux, Windows, Unix)
- Network devices (routers, switches, firewalls)
- Applications and services (web servers, databases, cloud services)
- Internet of Things (IoT) devices and embedded systems
The primary functions of a syslog client include:
- Capturing and formatting log messages based on predefined events or conditions.
- Determining the appropriate facility code and severity level for each log message.
- Sending log messages to one or more designated syslog servers using the syslog protocol (UDP or TCP).
Using Syslog with Various Operating Systems
Syslog is widely supported across various operating systems, making it a versatile solution for centralized log management in heterogeneous environments.
Linux Syslog
- syslogd: The original syslog implementation in Linux, which is now largely replaced by more modern alternatives.
- rsyslog: A popular and powerful syslog implementation for Linux that offers advanced features like reliable message queuing, TCP and UDP support, and extensive filtering and processing capabilities.
- syslog-ng: Another widely-used syslog solution for Linux that provides enhanced security, flexible configuration options, and support for various syslog formats and transports.
Windows Syslog
While Windows does not natively support syslog, there are several third-party solutions available:
- NXLog: A free and open-source log collection and forwarding tool that supports syslog and can be used on Windows systems.
- SolarWinds Log & Event Manager: A commercial syslog server solution for Windows that provides centralized log collection, analysis, and reporting.
- Snare for Windows: A free syslog forwarder that allows Windows systems to send event logs to a syslog server.
Unix Syslog
Unix-based operating systems, such as Solaris, AIX, and HP-UX, typically include a built-in syslog implementation similar to the original syslogd found in Linux.
Docker Syslog
Docker containers can be configured to send log messages to a syslog server, either by using the built-in syslog driver or by running a syslog agent inside the container.
Pros and Cons of Using Syslog
Pros of Using Syslog
- Centralized Log Management: Syslog allows you to collect and store log data from multiple sources in a centralized location, simplifying log analysis and monitoring.
- Standardized Protocol: The syslog protocol is a widely adopted standard, ensuring compatibility across various platforms and devices.
- Scalability: Syslog can handle large volumes of log data, making it suitable for environments with numerous log sources.
- Ease of Implementation: Syslog is natively supported by many operating systems and applications, making it easy to integrate into existing environments.
- Audit and Compliance: Centralized log management with syslog can help organizations meet regulatory compliance requirements by providing a comprehensive audit trail.
Cons of Using Syslog
- Limited Security: The syslog protocol lacks built-in security features, such as encryption or authentication, which can expose log data to potential eavesdropping or tampering.
- Limited Filtering and Processing: While syslog provides basic filtering and processing capabilities, more advanced features may require additional tools or third-party solutions.
- Potential Performance Issues: In high-traffic environments, syslog servers may experience performance bottlenecks, leading to log message loss or delays.
- No Guaranteed Delivery: When using UDP as the transport protocol, syslog does not guarantee reliable delivery of log messages, which can result in data loss.
- Limited Log Retention: Syslog itself does not provide long-term log storage or archiving capabilities, requiring additional solutions for log retention and management.
Tools such as Sematext Logs can help you overcome these limitations. Benefit from secure, reliable, and scalable log management solutions designed to meet your organization’s needs.
Syslog Use Cases
Syslog is a versatile log management solution that finds applications in various domains, including:
System and Network Monitoring
By collecting and analyzing syslog messages from servers, network devices, and applications, syslog enables effective monitoring of system health, performance, and availability. The standardized syslog format helps in identifying and correlating events across different platforms, enhancing the overall monitoring process.
Security Logging
Syslog can centralize security-related logs from firewalls, intrusion detection systems, and other security appliances, aiding in threat detection, incident response, and forensic analysis. Utilizing syslog for security logging ensures that critical security events are captured and stored in a syslog server for analysis.
Troubleshooting and Debugging
Centralized log management with syslog simplifies the process of identifying and resolving issues by providing a consolidated view of syslog data from multiple sources. Developers and system administrators can use detailed logs to pinpoint errors and debug issues efficiently, leveraging the different syslog severity levels to prioritize their efforts.
Compliance and Auditing
Many regulatory frameworks and industry standards require organizations to maintain comprehensive logs for auditing purposes. Syslog can help meet these requirements by providing a centralized log repository, ensuring that all relevant log data is available for compliance audits.
Internet of Things (IoT) and Embedded Systems
Syslog is well-suited for collecting and managing logs from IoT devices and embedded systems, enabling remote monitoring and diagnostics. By configuring these devices to forward logs to a syslog server, organizations can gain insights into their operational status and troubleshoot issues remotely.
Application Logging
Developers can integrate syslog into their applications to log events, errors, and debug messages. This facilitates easier troubleshooting and maintenance, as all application logs are centralized and can be analyzed using syslog analyzers.
Cloud and Containerized Environments
Syslog can be used to collect and manage logs from cloud-based services and containerized applications, providing a unified view of log data across distributed environments. Docker syslog integration allows containers to send logs to a central syslog server, ensuring consistency and ease of management.
Rsyslog and Syslog-ng
While syslog is the standard protocol for log management, two prominent implementations offer enhanced features and functionalities: rsyslog and syslog-ng.
Rsyslog
Rsyslog is an open-source syslog implementation that provides a robust and highly configurable solution for log management. It supports various input and output modules, allowing for log collection from diverse sources and integration with different storage backends. Rsyslog offers advanced features like reliable message queuing, TCP and UDP support, and powerful filtering and processing capabilities. It is widely adopted and is the default syslog implementation in many Linux distributions.
Syslog-ng
Syslog-ng (Next Generation) is another popular open-source syslog implementation known for its security, flexibility, and performance. It supports a wide range of log formats, transports, and authentication methods, making it suitable for complex and heterogeneous environments. Syslog-ng provides advanced features like content-based filtering, message rewriting, and load balancing. It emphasizes security by offering features like Transport Layer Security (TLS) encryption and message authentication. To streamline your log management and leverage the full potential of syslog, consider using tools like Sematext Logs. With its powerful centralized logging, advanced filtering, and real-time analytics, Sematext Logs can handle large volumes of data efficiently and securely.