What Is a SSL/TLS Handshake?
A Secure Sockets Layer (SSL) / Transport Layer Security (TLS) handshake is the process of creating a safe and secure encrypted communication channel between the client (user’s browser) and the server (web server). Thus, protecting user information and ensuring risk-free transactions by preventing an attacker (third party) from reading or changing the actual data.
SSL and its updated and more secure variant TLS are cryptographic authentication and encryption protocols. For instance, every time you visit a website, your browser and the web server will first authenticate each other and build a secure encrypted communication channel using SSL/TLS handshake.
[ebook_banner]
It helps prevent third parties, including your Internet service providers (ISPs), from intercepting sensitive data during a website visit. The objective is to authenticate the identities of the communicating parties so that a secure connection can be established and that the third parties can’t listen in or alter the conversation.
Useful SSL/TLS Terminology
Learning some of the essential terms is a prerequisite to delve into the specifics of the SSL/TLS handshake. Here are some of them:
Cipher Suite
A cipher suite is a collection of cryptographic algorithms used to establish a secure connection between the client and server. During the SSL/TLS handshake, both the client and host computer agree upon an encryption method from the cipher suites to create keys and encrypt information.The cipher suite contains digital signature algorithms, hash functions for checking if the data in transit is modified, asymmetric encryption algorithms for the handshake, and symmetric encryption algorithm to maintain session security.
Key Exchange
TLS key exchange allows two parties to use a cryptographic algorithm by exchanging cryptographic keys. For example, a symmetric session key is generated during SSL/TLS handshake before an encrypted message is transmitted. RSA and Diffie-Hellman-Merkle are the top key exchange algorithms used.
Symmetric Encryption
Symmetric encryption encrypts and decrypts using the same (one) key. Compared to asymmetric cryptography, this is more efficient – it needs less encryption time, uses fewer resources, and can transfer large volumes of data, while also maintaining confidentiality. Cipher text is the same or smaller than the plain text.
Some of the examples of widely-used symmetric encryption include Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), Advanced Encryption Standard (AES), more.
Asymmetric Encryption
Asymmetric encryption uses two keys: a public and a private key. This means a message encrypted with a public key can only be decrypted with the corresponding private key. It provides better security as the keys are never shared and allow the user to authenticate data using digital signatures. It is slower than symmetric encryption and can only be utilized for small amounts of data. Cipher text is the same or larger than plain text.
Some of the examples of widely-used asymmetric encryption include Rivest Shamir Adleman (RSA), Digital Signature Algorithm (DSA), the Diffie-Hellman exchange method, and more.
Authentication
Authentication lets each party in a communication verify that the other party is who they say they are. SSL/TLS handshake verifies the server’s credibility by comparing its public key with the digital signature issued by the SSL certificate authority, ensuring a client can trust the server’s identity.
How Does the SSL/TLS Handshake Work?
To perform secure communication, the SSL/TLS handshake involves several exchanges between the client and the server:
- Choose a protocol (TLS) version.
- Select a cipher suite.
- Verify each other by exchanging and confirming digital certificates.
- Create session keys to use symmetric encryption after the handshake is complete.
What Happens During a SSL/TLS Handshake: Step-by-Step Process
The exact steps needed to complete a SSL/TLS handshake depend on the encryption algorithm used, but the basic process is as follows:
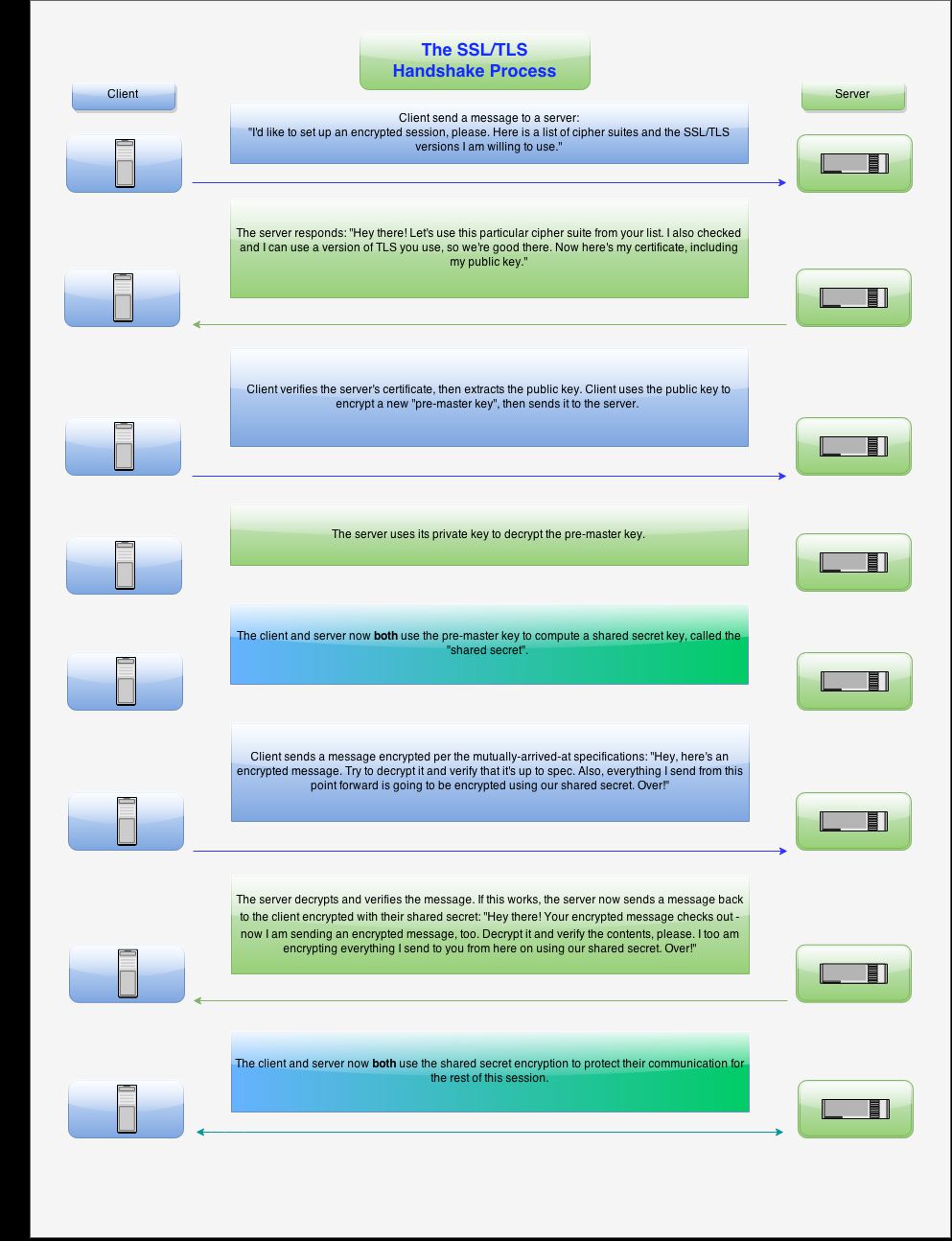
Image: SSL.com
- Step 1: The SSL/TLS client will send the server a “ClientHello” message that details the client’s configuration settings, including the SSL/TLS version, the cipher suites it supports, the data compression technique it employs, and a string of random data referred to as “client random.”
- Step 2: The SSL/TLS server sends back a “ServerHello” message containing its own public key, digital certificate, session identifier, the cryptographic algorithm agreement (selected by the server from the client-supplied list of algorithms), and the “server random”.
- Step 3: The client performs authentication by contacting the server’s certificate authority (CA) to validate the web server’s digital certificate. This confirms the authenticity of the web server, thus, establishing trust.
- Step 4: During the ClientKeyExchange step, the client extracts the public key from the verified certificate and generates a new random sequence called the premaster secret. The premaster secret is then encrypted using the extracted public key and is sent to the server.
- Step 5: The SSL/TLS server decrypts the premaster secret using its private key.
- Step 6: Both the client and the server now use the premaster secret to configure a shared secret key.
- Step 7: Next, the client sends an encrypted “finished” message using the shared secret key. This message says that the client’s part of the handshake is complete.
- Step 8: Finally, an encrypted “finished” message is sent back to the client from the server using the previously agreed shared secret key, which indicates the end of the server’s side of the handshake.
- Step 9: Once the SSL/TLS handshake and negotiation is done, the server and the client communication continues, i.e., they begin to share files and messages using the session keys (symmetric encryption).
Note: Few improvisations can be added such as verifying both the client and the server instead of just verifying the server.
What Happens if the SSL/TLS Handshake Fails?
The client and server can securely exchange data if the TLS/SSL handshake is successful. Otherwise, if a TLS/SSL handshake fails, the connection is terminated, and the client receives a 503 Service Unavailable error.
Sematext Synthetics or Experience can be used to monitor the connection and track the root cause as seen in the next section below.
Monitoring SSL/TLS Handshake with Sematext
Sematext Synthetics is an industry-leading synthetic monitoring tool with SSL/TLS monitoring capabilities.
With Sematext, you can monitor how long it takes to perform a TLS handshake for any HTTP request, as well as how the time taken for the TLS handshake compares to other parts of the HTTP request, such as the DNS lookup time or the HTTP download time.
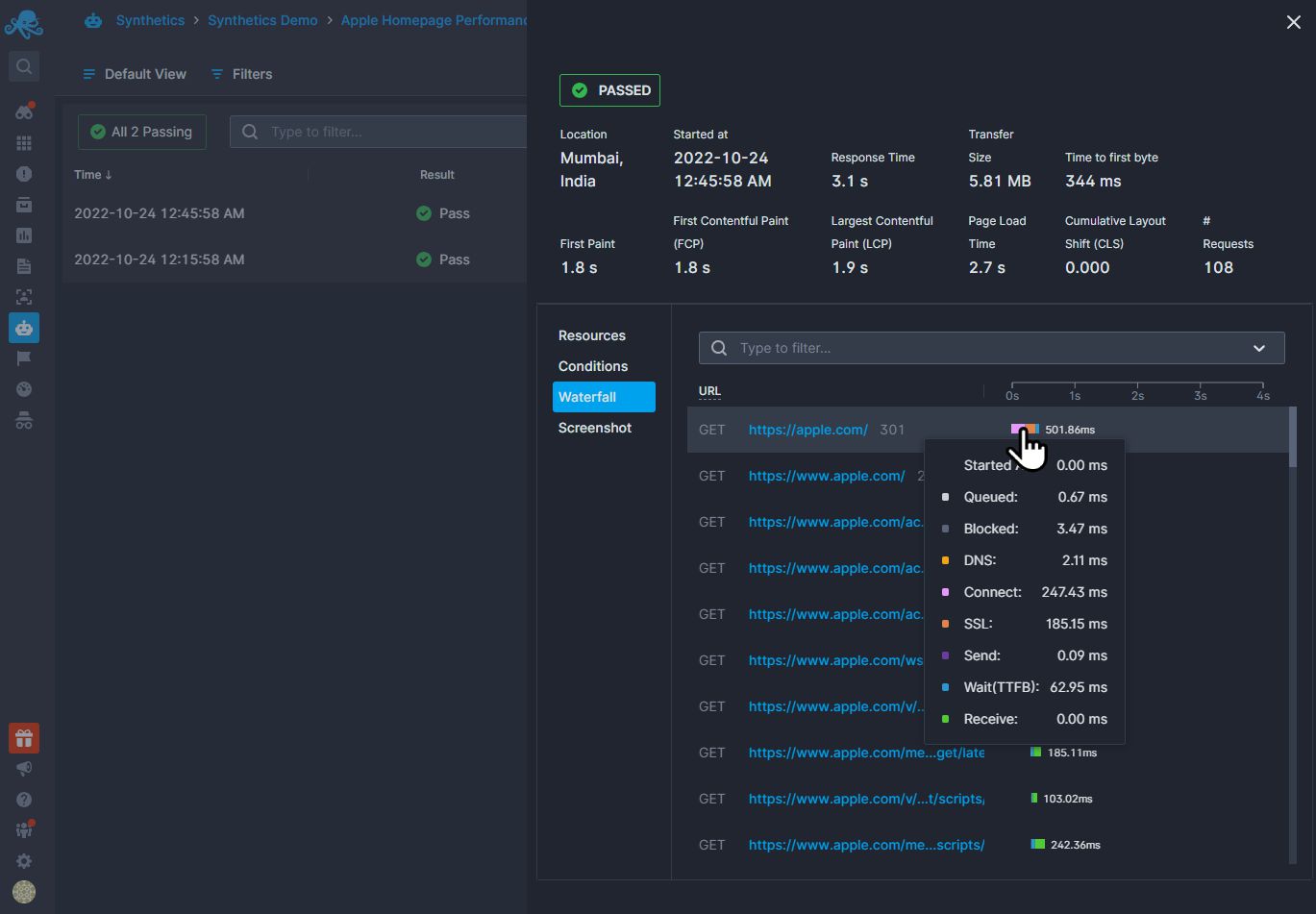
You can gather metrics from SSL/TLS handshakes made with your site and see if they are meeting SLAs. When handshakes are not falling within your parameters, Sematext will instantly send notifications to yourself, others, or entire teams via Slack, Twilio, Zapier, VictorOps, and many others.
Sematext Synthetics will also run tests to check for SSL certificate expiry on all your SSL/TLS certificates. These include checking your leaf, intermediate, and root certificates in the certificate chain.
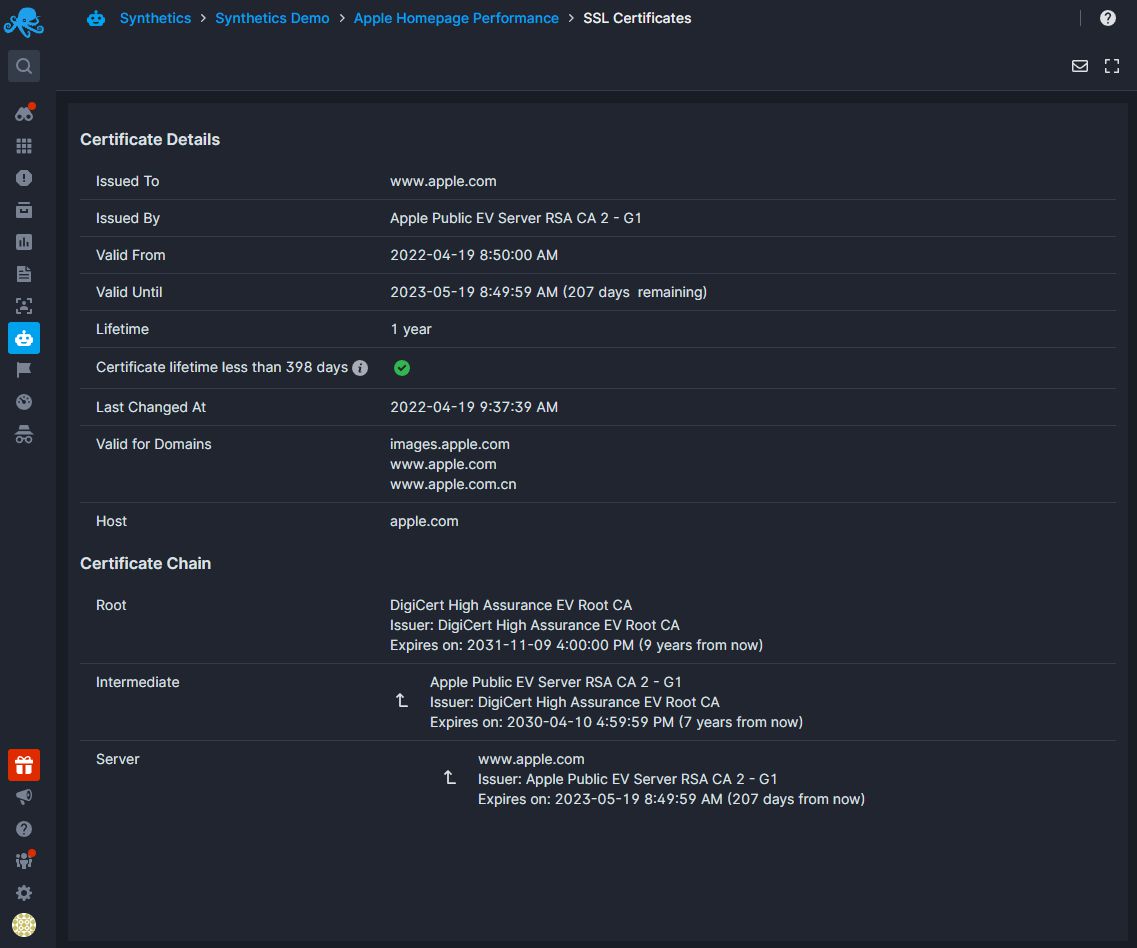
Start your 14-day free trial and see how Sematext Synthetics can help monitor your SSL certificate expiry. You can also learn more about it from the video below: