What Is an SSL Certificate Chain?
The certificate chain, also known as the certificate chain of trust, is an ordered list of digital certificates, including SSL/TLS certificates and Certificate Authority certificates, that verify a website’s or server’s authenticity and security to establish trust between browsers and servers.
The SSL certificates in a chain are issued by Certificate Authorities (CAs), trusted entities responsible for issuing, managing, and revoking SSL certificates. The SSL stands for Secure Sockets Layers, the protocol that enables the encrypted connection and communication between server and browser. While the SSL has been replaced by the much more secure TLS protocol, the two titles are interchangeably used to denote the chain of certifications issued between servers and users.
How Do SSL Certificate Chains Work?
SSL certificate chains establish a trust relationship called the “chain of trust” between the SSL certificate of a website and the certificate authority.
The root SSL certificate is issued by a trusted certificate authority, the entity responsible for issuing digital certificates that authenticate the identity of individuals, organizations, or devices.
If an SSL certificate is issued by a trusted CA, the client’s device will cross-checks the certificate with the list of trusted CAs to establish a secure connection down to the end of the certificate chain. The public key of the certificate is verified and validated through a SSL/TLS handshake protocol between the client (web browser) and the server. For this to work, operating systems and web browsers are equipped with a predefined list of trusted CAs.
Conversely, if the certificate wasn’t issued by a trusted CA, the client’s device will display an error message.
[youtube_video]https://www.youtube.com/watch?v=67Kfsmy_frM[/youtube_video]
Components of an SSL Certificate Chain
An SSL certificate chain consists of three types of certificates.
Server Certificate (Leaf Certificate)
A server or leaf certificate is a digital certificate issued to a web server by a CA for the domain the user wants to visit. This can be either an SSL (Secure Sockets Layer) or TLS (Transport Layer Security) certificate, depending on the encryption protocol used to establish the secure connection. Its main purpose is to verify the server’s identity and establish a secure encrypted connection between the server and the client’s web browser.
These certificates are identifiable by the “HTTPS” and padlock you see before the domain name when you visit a website via a browser. The “S” indicates that the site can have a secure encrypted connection with the server. Conversely, an “HTTP” at the start of your URL indicates an invalid server certificate or an encryption failure which can lead to security risks for the user. Such certificates are usable by multiple network server types, including web and email servers.
Intermediate Certificate
The intermediate certificate, also known as the chain certificate, acts as the middleman between the root and end server certificates. These certificates sign your server SSL/TLS certificate, and, in turn, are signed by the private key of the root certificate that issued it, in order to establish trust.
All certificate chains must contain at least one intermediate certificate, and it must be installed on the server to ensure its compatibility with all clients—from browsers, to mobile devices, and applications. The trustability of an intermediate CA is tied to its linkage to the root CA.
Root Certificate Authority (Trusted CA Certificate)
The root certificate is issued and always signed by the Certificate Authority. They are the most important ones in the chain as their role is to issue intermediate CAs as well as to sign, verify, and provide third-party validation for other SSL certificates within the chain. Which is why they should be highly regulated and audited to ensure their trustworthiness.
The root CA is by default preloaded and preinstalled in the “trust stores” of browsers and operating systems. Thus allowing them serve as the foundation of trust for your online security protocols.
How Many Certificates Are in the SSL Certificate Chain?
An SSL certificate chain consists of at least three certificates. However, depending on the organization’s policy and security protocol, the chain could have more intermediate or leaf certificates. Regardless of the number, each certificate in the chain of trust is digitally signed and identified by the next one to verify the authenticity of the SSL certificate.
What is the Correct SSL Certificate Chain Order?
The correct SSL certificate chain order is the order in which the certificates are arranged in the chain to establish trust between the client and server. It starts with the root certificate, followed by the intermediate certificates, and ending with the server certificate. This also corresponds to the certificate chain hierarchy.
However, from a client’s perspective, the order will progress from the server certificate to the root CA. By client’s perspective, we mean when a client (web browser) tries to connect with a server (website). The server presents a server certificate that has been signed by the trusted intermediate to the clients. This trusted intermediate also needs to be signed by the trust root CA.
The correct SSL certificate chain order is important as it ensures that the server certificate is authenticated and verified against the Intermediate certificate which is, in turn, authenticated against the public key of the root certificate.
SSL Certificate Chain Example
The digital certificate chain forms a tree-like structure with both the root and the leaf certificates completing this structure. It is important to note that everything ends with the root CA which verifies the entire chain.
Let’s take https://sematext.com/ as an example and explore the certificate chain.
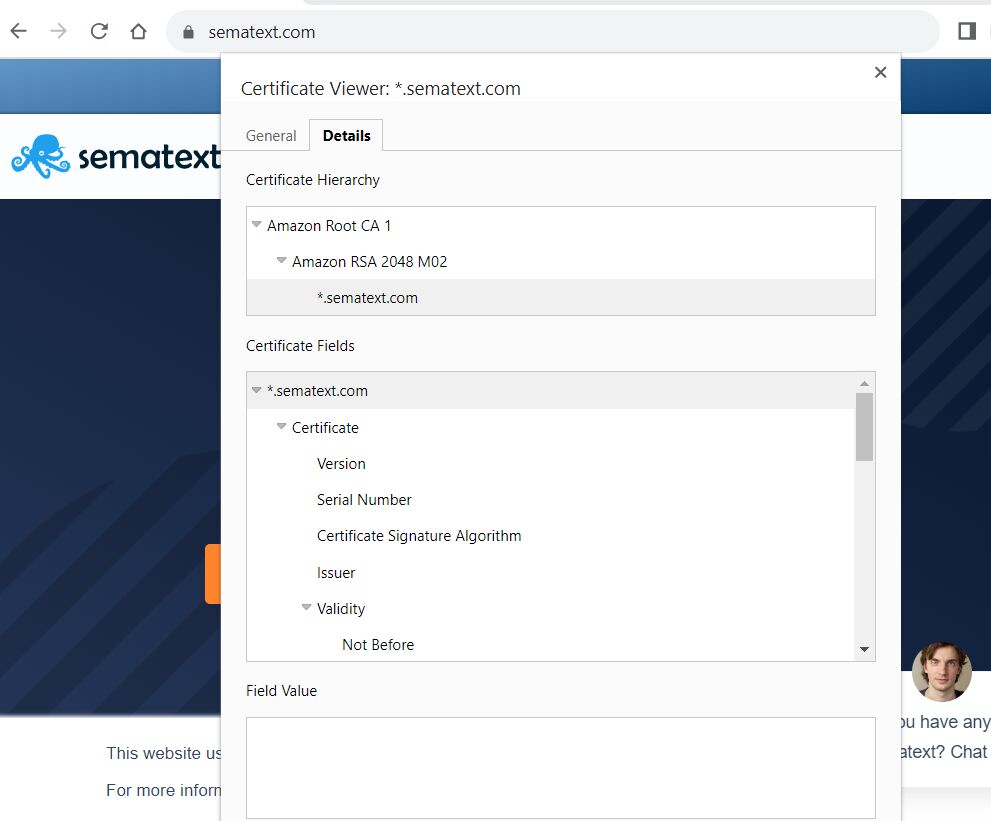
Here we can see three certificates:
- Amazon Root CA 1 is the root certificate, the most important in the chain. If the CA issuing it is distrusted or revoked, the chain of trust is broken.
- Amazon RSA 2048 M02 is the intermediate certificate issued to protect the root certificates and for issuing end server and leaf certificates.
- *.sematext.com is the SSL leaf certificate. This public certificate is issued by Amazon RSA 2048 M02, the intermediate certificate, and never directly by the root certificate as this would involve several security risks..
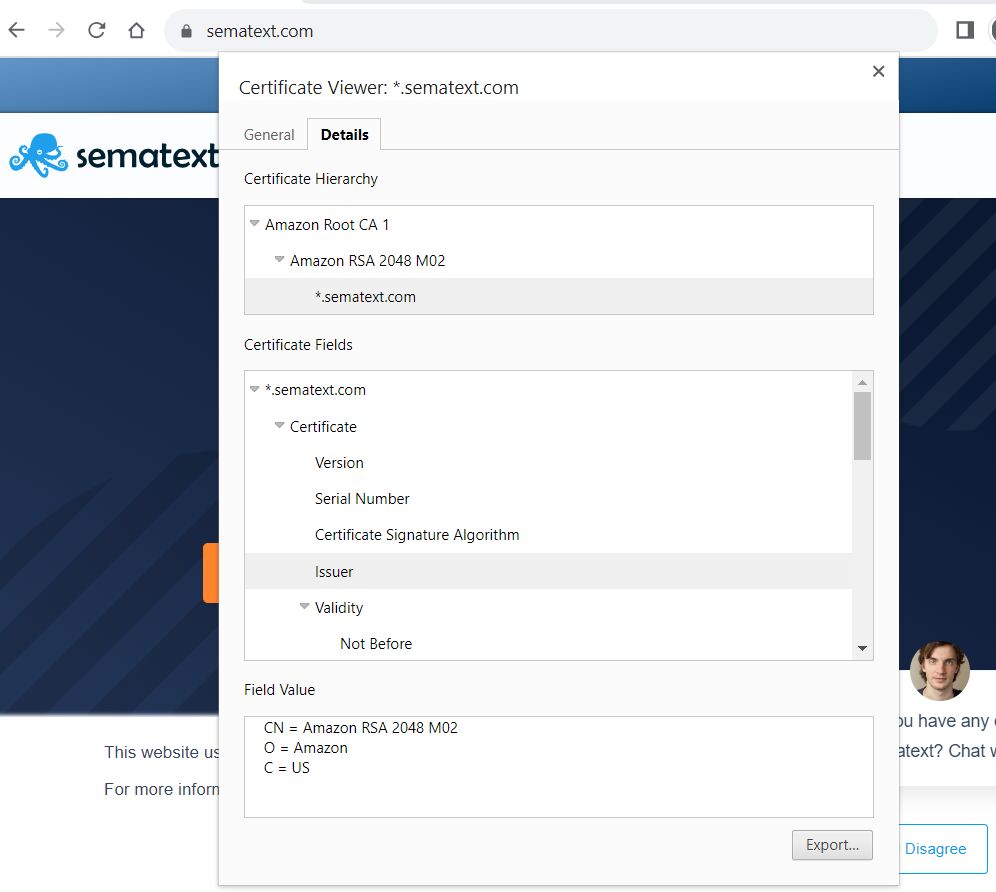
Amazon CA 1 is one type of root CA operated by Amazon Trust Services. Amazon Trust Services is a certificate authority (CA) managed by Amazon (AWS) and provides, issues, and deploys certificate classes to organizations worldwide. This means that it can be explicitly trusted
Amazon public certificates are requested by the IT team through AWS Certificate Manager (ACM) from Amazon Trust Services, which uses a structured trust hierarchy.
The public leaf certificate issued to you is chained to one or more intermediate CAs. The intermediate CAs are then chained to the root certificate, which is then chained to Amazon Trust Services root CA. The latter is trusted by default by most browsers and operating systems. If any one of the SSL certificates is invalid, broken, or has been revoked, your certificate won’t be trusted by clients’ devices.
How Is an SSL Certificate Chain Validated?
When visiting a website, in our case, https://sematext.com/, a user connects to our server over HTTPS. Before the website is loaded, the site server sends its certificates.
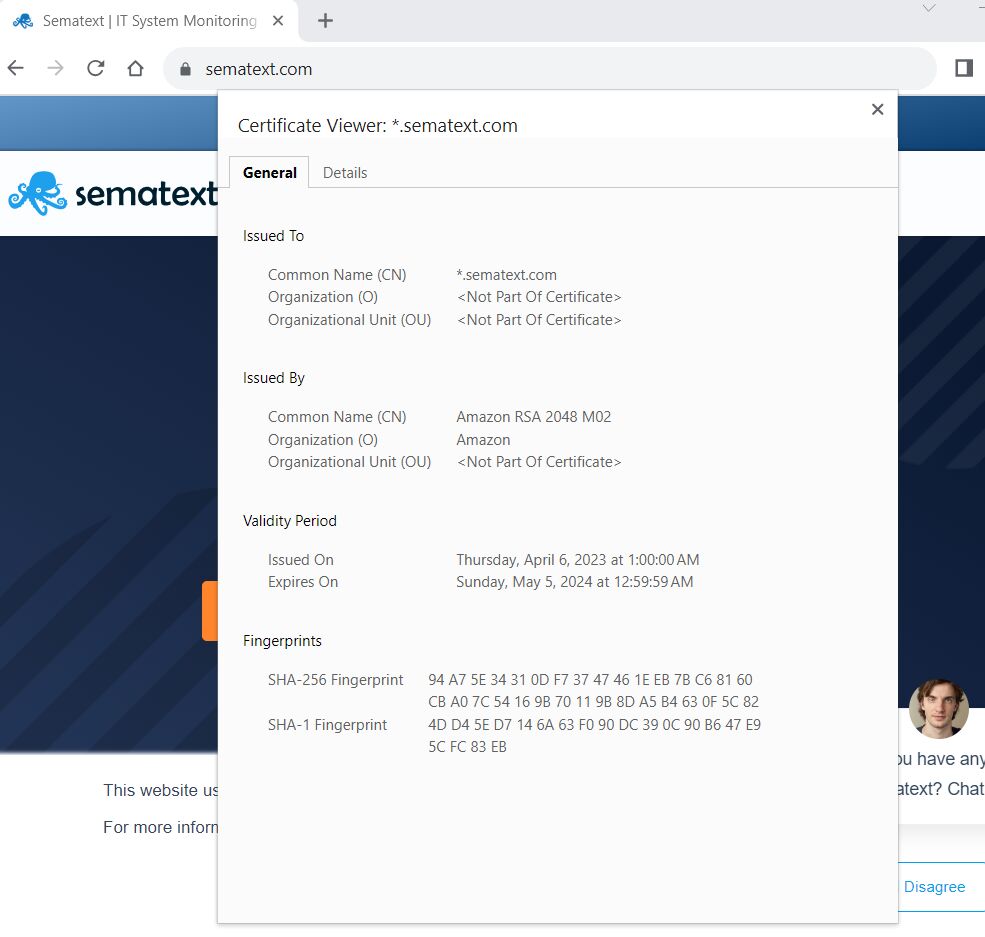
Such a certificate contains information like:
- Who it was issued to
- The entity that issues the leaf certificate (*.sematext.com )
- The date of its issuing and the validity period
- Whether the certificate has been revoked or is invalid
- The certificate’s fingerprints, which are calculated based on its containing data and its signature.
This is the process of verifying and validating a certificate’s legitimacy, authenticity, and trustworthiness in the SSL certificate chain:
- The client checks the leaf certificate to ensure it is still valid and was issued by a trusted CA.
- The domain name is checked to ensure that it matches the domain name of the server it connects to.
- If the leaf certificate is passed the client checks each intermediate certificate by verifying if each signature has been issued by the previous certificate.
- The client checks if the root certificate can be trusted by verifying if the root certificate’s signature is stored in the client’s trusted root store.
If all the certificates check out, the chain is considered valid and establishes a secure encrypted connection with the server. Thus, the website loads with a padlock symbol and “HTTPS” in the URL bar.
What Happens if the Chain of Trust Verification Process Fails?
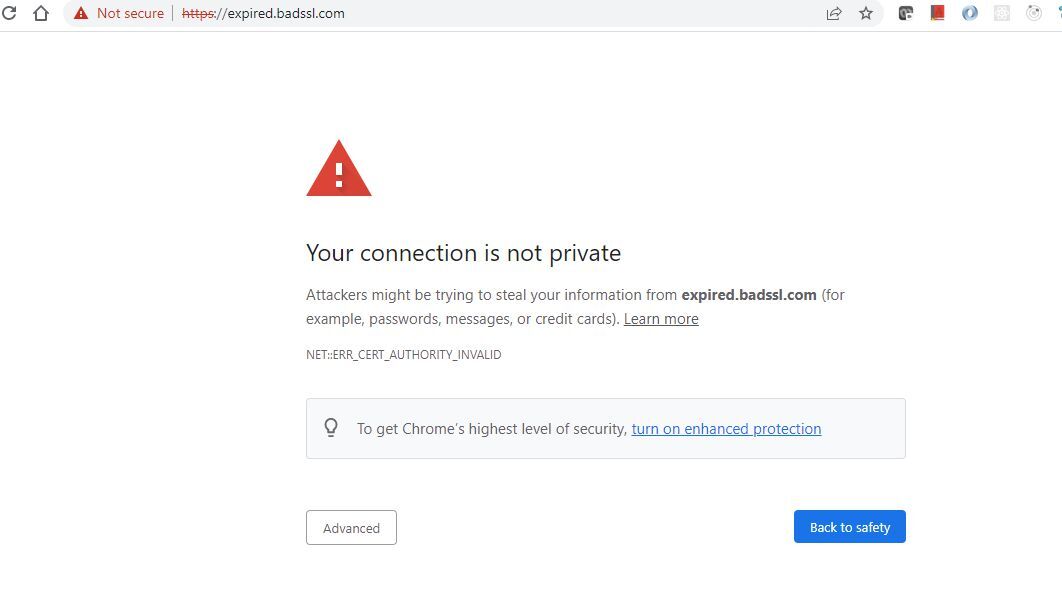
If the chain of trust verification process fails, the web browser displays the “Your connection is not private”, “Not Secure”, or “Warning: Potential Security Risk Ahead” messages to the client. The SSL certificate error warning message featured depends on the browsers used.
Chrome Browser:
Firefox Browser:
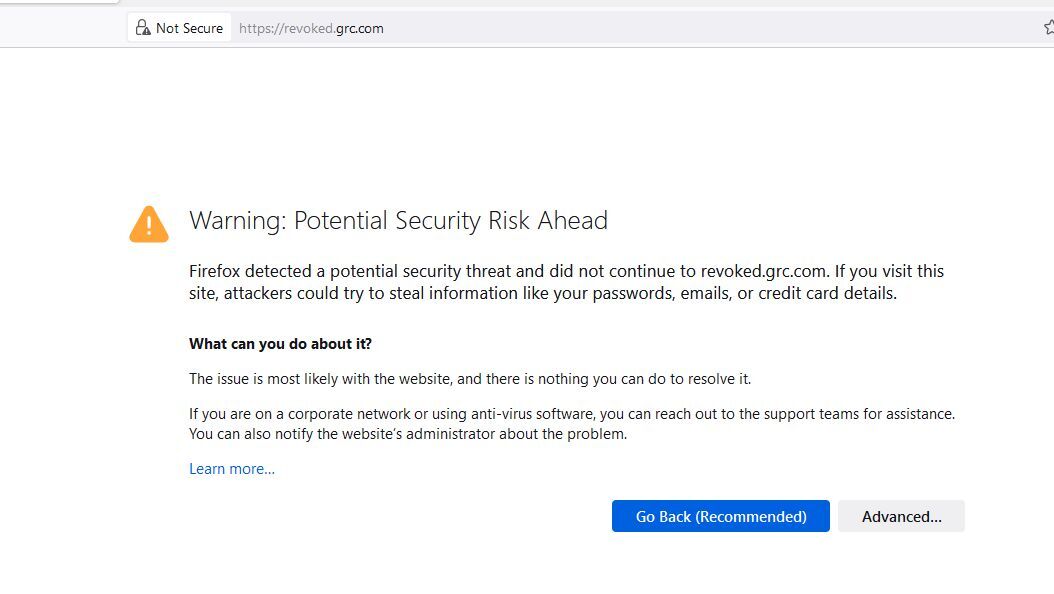
This warning message indicates that the connection may not be secure and that the server cannot verify the authenticity of the SSL/TLS certificate.
Why this may happen:
- An incorrect domain name on the user’s part,
- A revoked or expired certificate on the company’s IT team’s part, or
- An invalid digital signature on the company’s IT team’s part.
When this happens, it is advisable for clients to leave the site. If they do not exit, they proceed at their own risk and are vulnerable to malware, data theft, phishing and Man-in-the-middle attacks.
How to avoid SSL Certificate Chain Issues
SSL certificate chain problems arise when your client’s web browser cannot verify the SSL certificate returned by your server. This has implications for your brand, your website’s SEO ranking, and the overall user experience of your site.
To steer clear of these issues, you can explore a few options. This includes ensuring your SSL is properly installed, renewing before your certificate expires, and using a tool with SSL management functionalities. Irrespective of the specific issue or solution you opt for, effective SSL certificate management requires active SSL monitoring, which is why it is highly recommended.
Tools with SSL/TLS certificate monitoring capabilities help you keep tabs on your certificate’s availability, validation, expiration dates, and any changes to their functionality and accessibility.
[product_banner type=”synthetic-monitoring”]Get alerted about any SSL certificate issues and before expiration.[/product_banner]
SSL Certificate Monitoring with Sematext
Sematext Synthetics is a comprehensive solution designed to monitor various aspects of your websites’ performance, including SSL certificates.
SSL certificate validation is one central aspect of Sematext Synthetics. By leveraging Google Chrome, the Synthetics Browser monitor simulates user behavior and loads your websites. This process enables it to perform real-time SSL certificate checks on all the certificates in the chain, including the leaf, intermediate, and root certificates. By doing so, the tool can identify and alert you to any errors or issues before they impact your end-users.
Additionally, Sematext Synthetics excels in certificate change detection. It continuously monitors your SSL certificates every 10 minutes and promptly alerts you whenever a change is detected. These alerts include detailed reports, allowing you to investigate the changes and ensure the integrity and security of your certificates.
Watch the video below to see how Sematext Synthetics can effectively monitor your SSL certificates, or start your 14-day free trial to experience it yourself!