Note: This is a guest post by Jochen Kressin, the CTO of floragunn GmbH, the makers of Search Guard, an open-source X-Pack Security alternative.
In this article, we show you how to secure Elasticsearch and Kibana for free using the Community edition of Search Guard. We start with a vanilla Elasticsearch and Kibana setup, install and configure Search Guard for Elasticsearch, and use the Search Guard Kibana plugin to add session management capabilities to Kibana.
Prerequisites
As a prerequisite, install the latest Elasticsearch and Kibana version.
Installing Elasticsearch
https://www.elastic.co/guide/en/elasticsearch/reference/current/setup.html
Installing Kibana:
https://www.elastic.co/guide/en/kibana/current/setup.html
Installing Search Guard
Search Guard is an Elasticsearch plugin, and can thus be installed by using the standard plugin installation procedure of Elasticsearch.
First, figure out which version of Search Guard you need for your Elasticsearch installation. Due to compatibility checks in Elasticsearch, the version of Search Guard must match the version of Elasticsearch exactly. So if you run Elasticsearch 5.4.0, you need to install Search Guard 5.4.0. Other versions will not work. If in doubt, you can always refer to our version matrix, which lists all available versions of Search Guard. In this tutorial, we use Elasticsearch and Kibana 5.4.0.
First, stop all running nodes, change to the installation directory of Elasticsearch and install Search Guard:
bin/elasticsearch-plugin install -b com.floragunn:search-guard-5:5.4.0-12
The plugin will be downloaded from Maven and installed automatically. Once the installation is complete, you will find a new folder plugins/search-guard-5 in your Elasticsearch installation directory.
Configuring TLS
Search Guard makes heavy use of TLS to encrypt and secure the complete traffic in your cluster. In order for TLS to work, you need to generate and install TLS certificates on all nodes. This makes sure that no one can sniff or tamper with your data, and that only trusted nodes can join the cluster.
There are several ways of generating the necessary certificates, but for this quickstart tutorial we will use the demo installation script that ships with Search Guard. For other ways of generating certificates, please refer to the section “Configuring Search Guard SSL” of the official Search Guard documentation.
In order to execute the demo installation script, change to the directory
<ES installation directory>/plugins/search-guard-5/tools
and execute the script
install_demo_configuration.sh
Depending on which platform you are on, you may need to set execution permissions first. The script will generate the TLS certificates and add the corresponding configuration settings to the elasticsearch.yml file. Once this is finished, you can start your nodes again.
Initializing Search Guard
After your nodes are up, you need to initialize Search Guard. In this tutorial, we will use the sample configuration files that ship with Search Guard. They already contain the correct users, roles and permissions for the Kibana integration.
The configuration files are located in this directory:
<ES installation directory>/plugins/search-guard-5/sgconfig
In order to upload this configuration to Search Guard, you can either use the sgadmin command line tool, or the REST management API. When using the sgadmin command line tool, you need to specify various parameters, such as the path to your certificates or the name of your cluster. You can read all about sgadmin in the official documentation.
For our quick start tutorial, we will use the demo sgadmin script, which already contains all required parameters. Change to:
<ES installation directory>/plugins/search-guard-5/tools
and execute the script
sgadmin_demo.shAs with the installation script, you might need to set execution permissions first. After the script has been executed, Search Guard is initialized and your cluster is fully secured by TLS.
You can verify that everything works as expected by visiting the following URL with a browser:
https://localhost:9200/_searchguard/authinfo
Since we are using self-signed certificates, ignore the browser warning and accept the Root certificate that Search Guard is using. The warning message varies from browser to browser. Note that because TLS is now enabled on the REST layer, you have to use https when talking to Elasticsearch. Connecting with unsecured http will not work anymore.
When prompted for a username and password, you can use admin/admin. This user has full access to the cluster and all indices. You should see information about the currently logged in user in JSON format.
Congratulations, Search Guard is now installed and configured properly.
If you want to learn more about the structure and contents of the configuration files, refer to chapter Search Guard configuration of the documentation. After you make changes to the configuration, simply execute sgadmin_demo.sh again for the changes to take effect.
Adding Kibana Security Plugin
As with Elasticsearch, Kibana does not provide any security or session management out of the box. As the first step, we will configure Kibana so that it is able to talk to our Search Guard secured cluster. In the second step, we will install the Search Guard Kibana plugin which adds session management capabilities.
Securing Kibana
For Kibana to work with a Search Guard secured cluster, we need to make some adjustments in the kibana.yml configuration file. First, change the default Elasticsearch URL from http to https:
elasticsearch.url: "https://localhost:9200"
And since we are using self-signed certificates in this tutorial, we need to tell Kibana to accept them explicitly by disabling certificate verification:
elasticsearch.ssl.verificationMode: none
This is of course not recommended for production. In production, you would rather install and configure your Root CA in Kibana, but that’s out of the scope of this tutorial.
Kibana is using a service user under the hood to manage the Kibana index, check the cluster health etc. This service user has to be present in Search Guard, and it needs to have the correct permissions to execute all required actions. The demo configuration already contains such a service user. The username and password of this user is “kibanaserver”. To tell Kibana to use these credentials when talking to Elasticsearch, add the following lines to kibana.yml:
elasticsearch.username: "kibanaserver" elasticsearch.password: "kibanaserver"
These are the minimal changes you need to perform. You can now start Kibana again and check that the connection to Elasticsearch works correctly.
Installing the Kibana Security Plugin
If you now try to access Kibana, you will see a Basic Authentication dialog popping up. This works, but we’d like to have a proper Kibana login dialogue and the possibility to logout again, without closing the browser. This is where the Kibana plugin comes into play.
As with Search Guard, you need to install the plugin that matches your Kibana version exactly. In our case, this is version 5.4.0-2. You can find all available versions on the GitHub release page:
https://github.com/floragunncom/search-guard-kibana-plugin/releases
Stop Kibana and download the zip file of the plugin to a directory on your machine:
After that, install it like any other Kibana plugin: Change to the Kibana installation directory and execute:
bin/kibana-plugin install file:///path/to/searchguard-kibana-5.4.0-2.zipThis will install the plugin, and run the Kibana optimizer afterwards. This may take a couple of minutes. After that, restart Kibana and access it via
You will be redirected to the login page and are prompted to provide username and password.
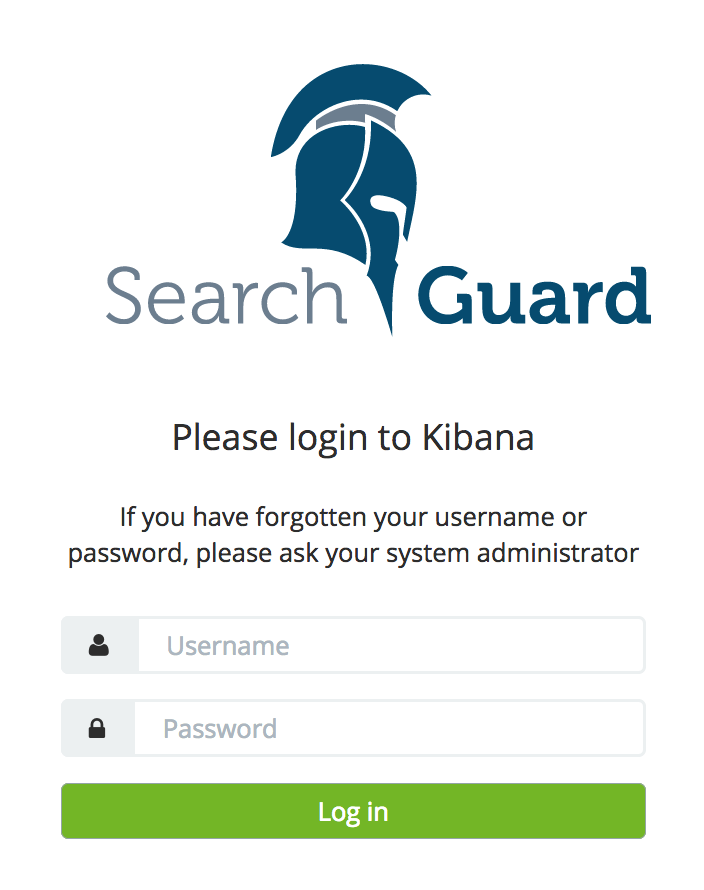 Use the demo Kibana user to login, the username and password is “kibanaro”. This user is mapped to the role sg_kibana and has access to all indices.
Use the demo Kibana user to login, the username and password is “kibanaro”. This user is mapped to the role sg_kibana and has access to all indices.
That’s it. Both Elasticsearch and Kibana are secured with Search Guard.
Where to go next?
Deep-dive into Search Guard by reading the official documentation:
https://github.com/floragunncom/search-guard-docs
Learn more about integrating Kibana and Search Guard:
https://github.com/floragunncom/search-guard-docs/blob/master/kibana.md
Add Kibana multi tenancy to separate dashboards and visualizations
https://github.com/floragunncom/search-guard-docs/blob/master/multitenancy.md
Ask questions on the Search Guard Google Group:
https://groups.google.com/forum/#!forum/search-guard
Read about our fair, flexible and affordable enterprise license model:
https://floragunn.com/searchguard/searchguard-license-support/
Follow us on Twitter to stay up-to-date with new releases and features:
https://twitter.com/searchguard